Network Penetration Testing: An In-Depth Exploration
Network penetration testing stands as a crucial practice for identifying vulnerabilities and security gaps within an organization's network, aiming to fortify its defenses against cyber threats. By simulating attacks that a malicious actor might exploit, cybersecurity professionals can uncover critical insights into how to enhance network security measures.
This comprehensive exploration delves into the methodologies employed by cybersecurity professionals to detect and address security gaps. The process not only prevents potential financial losses but also safeguards sensitive information from those seeking to gain unauthorized access, thereby maintaining the integrity and reputation of the organization.
Understanding Network Penetration Testing
At its core, network security testing is a methodical approach undertaken by cybersecurity professionals to identify and exploit security gaps, aiming to prevent malicious actors from gaining unauthorized access. This practice is pivotal in highlighting vulnerabilities and security flaws within a network's architecture.
Definition and Scope
Network penetration testing, often referred to as network pen testing, is a security exercise designed to evaluate the resilience of a network's defenses by simulating an attack from malicious entities. The scope of this testing encompasses various strategies and tools to identify weaknesses that could be exploited by attackers, offering critical insights for enhancing network security.
The Network Penetration Testing Process
Information Gathering
The initial phase of network pen testing involves thorough information gathering about the target environment. This step is crucial for understanding the landscape of the network, including identifying devices, services, and applications that are part of the network's infrastructure. Such information lays the groundwork for subsequent testing phases.
Planning and Vulnerability Scanning
Following the collection of detailed information, the next step is planning and conducting vulnerability scanning. This phase aims to identify potential weaknesses within the target environment's security posture. It involves the use of automated tools to systematically scan for vulnerabilities that could be exploited by attackers.
Automated vs. Manual Testing
This type of security testing employs both automated tools and manual techniques to uncover potential security issues. Automated tools are efficient for scanning a wide range of vulnerabilities quickly, whereas manual testing allows for a deeper, more nuanced exploration of complex security weaknesses that automated tools might miss.
Analysis and Reporting
Once testing is completed, the next critical step is the analysis and reporting of findings. This involves documenting the discovered security gaps and presenting them in a format that is actionable for stakeholders. This phase ensures that identified vulnerabilities are understood and addressed appropriately.
Remediation and Retesting
Addressing the identified technical vulnerabilities is a pivotal step in the network pen testing process. Remediation efforts are undertaken to patch or mitigate these weaknesses, followed by retesting to ensure that the fixes are effective and that no new vulnerabilities have been introduced during the remediation process.
Types of Penetration Tests
Cybersecurity professionals employ various types of penetration tests, including application penetration testing and vulnerability management, as part of a comprehensive security testing program. These tests are tailored to meet the specific security needs of an organization.
Black Box, White Box, and Gray Box Testing
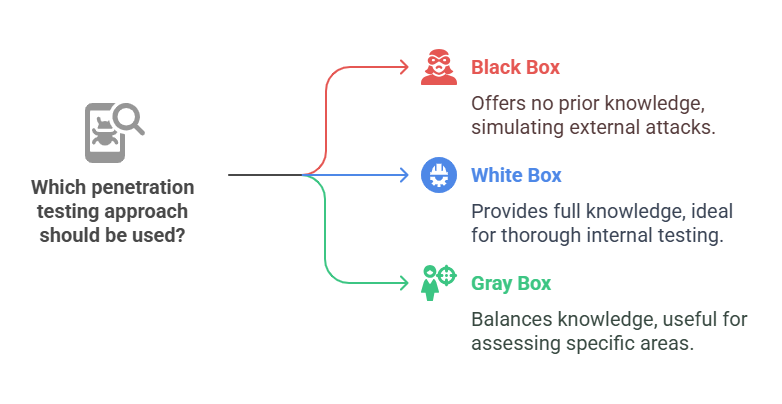
Different approaches such as black box, white box, and gray box pen tests offer varied levels of access and information to the testers. These methodologies help in identifying vulnerabilities from different perspectives, simulating various attack scenarios to provide a thorough assessment of network security.
Internal vs. External Penetration Testing
Network penetration testing can be categorized into external and internal tests. External network penetration testing focuses on identifying vulnerabilities that could be exploited from outside the network, whereas internal penetration testing assesses risks from within the organization. This comprehensive testing process ensures a holistic security evaluation.
The Importance of Network Penetration Testing
Network penetration testing plays a vital role in bolstering an organization's security posture, identifying vulnerabilities before they can be exploited by attackers, and ensuring compliance with regulations like PCI DSS.
Enhancing Security Posture
Through the identification and remediation of vulnerabilities, network penetration testing significantly enhances an organization's security posture, making it more resilient against cyber attacks.
Regulatory Compliance and Protecting Sensitive Data
Adhering to standards such as PCI DSS is essential for organizations handling sensitive data. Network penetration testing ensures compliance with these regulations, thereby protecting against data breaches and potential penalties.
Identifying and Mitigating Security Vulnerabilities
Vulnerability scanners play a crucial role in network penetration testing by pinpointing security gaps that cyber attackers could exploit. These tools enable cybersecurity professionals to identify and assess the severity of vulnerabilities, providing a roadmap for prioritization and remediation. By systematically identifying and mitigating these vulnerabilities, organizations can significantly reduce their attack surface, making it harder for attackers to exploit vulnerabilities and gain unauthorized access.
Preventing Financial Loss and Maintaining Reputation
Network penetration testing is instrumental in safeguarding an organization's financial stability and reputation. By identifying and addressing security risks before they are exploited, companies can avoid the costly consequences of data breaches, including regulatory fines, litigation costs, and loss of customer trust. Regular penetration testing demonstrates a commitment to security, helping to maintain and enhance an organization's reputation in the marketplace.
The Benefits of Performing Network Penetration Testing
Carrying out network penetration tests offers invaluable benefits by uncovering security risks, allowing cybersecurity professionals to fortify the network against potential attacks. This proactive approach is fundamental in building a resilient security posture.
Improved Security Measures and Controls
Frequent network penetration testing leads to the continuous improvement of security measures and controls. It enables organizations to adapt their defenses in response to evolving cybersecurity threats and tactics. Implementing the recommendations from penetration testing reports strengthens the security infrastructure, making it more difficult for attackers to succeed.
Prevention of Data Breaches and Network Intrusions
One of the most significant benefits of network penetration testing is the prevention of data breaches. By simulating cyber-attacks, organizations can identify and rectify security weaknesses before they can be exploited by malicious actors. This proactive measure effectively reduces the likelihood of network intrusions, safeguarding sensitive information from unauthorized access and ensuring data integrity and confidentiality.
Insights into Security Weaknesses
Network penetration testing offers deep insights into an organization’s security weaknesses, revealing vulnerabilities that might not be detected through conventional security audits. This process allows for the identification of multiple vulnerabilities across network devices, applications, and systems, providing a comprehensive view of potential security threats and enabling targeted improvements to the security framework.
Enterprise Security Built for Small Business
Network penetration testing is not just for large enterprises; it's equally vital for small businesses. It offers a scalable solution to identify and mitigate potential security threats that could otherwise devastate a smaller organization. By tailoring the testing process to the specific needs and resources of a small business, cybersecurity measures can be effectively implemented, providing robust security without the need for enterprise-level resources.
Steps in the Network Penetration Testing Cycle
The network penetration testing cycle involves several key steps, from initial consultation to reporting and follow-up, ensuring a thorough examination and strengthening of the network's security posture.
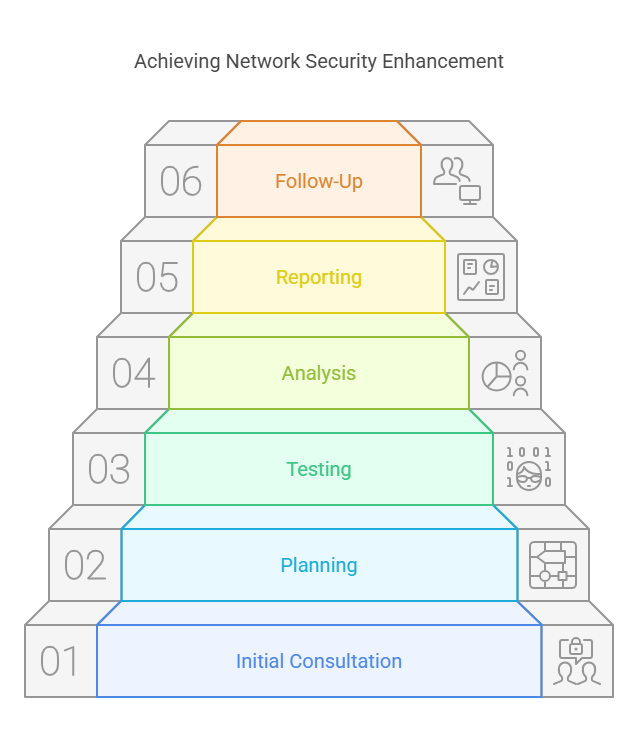
Initial Consultation and Goal Setting
The initial phase of network penetration tests involves consulting with the client to understand their network infrastructure, identify critical assets, and set specific goals. This stage is crucial for establishing the scope of the test, including the identification of security controls, phishing attacks, and potential security vulnerabilities. By aligning the testing process with the client's expectations and industry security standards, a targeted approach can be developed to address identified vulnerabilities effectively.
Understanding Client Expectations
Understanding client expectations is fundamental in the initial consultation phase of network penetration testing. This dialogue helps define the scope, targets, and objectives of the test, ensuring that the process aligns with the client’s security concerns and requirements. It sets the stage for a customized testing strategy that focuses on the client's most critical assets and potential security risks, aiming to strengthen their overall security posture.
Reconnaissance and Discovery Phase
The reconnaissance and discovery phase is a critical step in network penetration testing, where testers gather information about the target network. Through vulnerability assessments, testers identify exploitable weaknesses in the system's defenses. This phase lays the groundwork for developing a strategic approach to the penetration test, focusing on areas where the network is most vulnerable to attack.
Execution of Pen Tests
The execution phase of penetration testing involves actively exploiting identified vulnerabilities to assess the network's defenses. This crucial step determines the real-world effectiveness of existing security measures.
Technical and Human Approaches
Penetration testing combines technical and human approaches to evaluate network security comprehensively. Technical methods involve using software tools to automate the scanning and exploitation of vulnerabilities, while human approaches leverage social engineering tactics, such as phishing emails, to mimic the actions of cyber attackers. This blend of techniques ensures a thorough assessment of both the network's technical defenses and the organization's readiness against social engineering threats.
Reporting, Recommendations, and Follow-Up
Following the execution of penetration tests, the findings are compiled into a detailed report, offering actionable recommendations for improving network security. This stage is critical for closing security gaps and enhancing the network's defense mechanisms.
Sample Network Pen Test Report
A sample network penetration test report typically includes an executive summary, methodology, findings, and recommendations. It details the vulnerabilities discovered, such as SQL injections, brute force attacks, and the effectiveness of phishing emails. The report also assesses the risk level of each finding and proposes remedial actions to prevent unauthorized access to the target, providing a roadmap for strengthening the network's security posture.
Free Penetration Testing Policy Template
Offering a free penetration testing policy template empowers organizations to establish a foundational framework addressing technical vulnerabilities within their network. This template serves as a starting point, guiding businesses through the essential elements of a comprehensive penetration testing policy. It ensures that all aspects of the testing process are covered, fostering a secure and resilient network environment.
Letter of Attestation (LOA) and Certification
Upon the successful completion of a penetration test, a Letter of Attestation (LOA) and certification are provided. These documents serve as a testament to the organization's commitment to security, verifying that the network has been rigorously tested against known vulnerabilities. They instill confidence among stakeholders and customers, assuring them that the network's integrity meets high security standards.
Common Network Security Threats Addressed
In the realm of network security, penetration testing plays a critical role in safeguarding against threats such as malware, phishing, DDoS attacks, and more. By simulating real-world attacks, experts can identify and rectify vulnerabilities, thereby protecting sensitive data from unauthorized access. This proactive approach is indispensable in an era where cyber threats are continuously evolving.
Malware and Phishing Attacks
Malware and phishing attacks are prevalent threats that seek to exploit network vulnerabilities to steal sensitive information. Penetration testing helps in identifying potential security gaps that could be leveraged by attackers to deploy malware or execute phishing campaigns. By addressing these vulnerabilities, organizations can significantly reduce the risk of such attacks.
DDoS Attacks and Advanced Persistent Threats (APTs)
DDoS attacks and Advanced Persistent Threats (APTs) represent sophisticated challenges to network security. These attacks aim to disrupt services or stealthily infiltrate networks over extended periods. Penetration testing enables organizations to detect and mitigate the risk of these threats, thereby safeguarding the continuity and integrity of business operations.
Drive-by Downloads and DNS Attacks
Drive-by downloads and DNS attacks are insidious methods attackers use to compromise networks. Through penetration testing, vulnerabilities that could be exploited by these attacks are identified and remediated. This preemptive action helps in preventing unauthorized access and the potential manipulation of DNS entries, thus maintaining the network's security posture.
Tools and Technologies for Network Penetration Testing
The landscape of network penetration testing is enriched with a variety of tools and technologies designed to identify and exploit vulnerabilities. These tools, ranging from automated scanners to sophisticated testing software, enable security professionals to simulate attacks under controlled conditions. Their usage is crucial for uncovering weaknesses before they can be exploited by malicious actors.
Automated Tools and Software
Automated tools and software play a pivotal role in the efficiency and effectiveness of network penetration testing. These solutions expedite the process of detecting vulnerabilities, allowing for a more comprehensive assessment in a shorter timeframe. Automation also aids in the repetitive and meticulous tasks required in penetration testing, ensuring no stone is left unturned.
Integrations and Use Cases
The integration of penetration testing tools into the broader security ecosystem enhances the overall effectiveness of security strategies. These tools can be tailored to specific use cases, providing targeted insights into vulnerabilities and potential attack vectors. Such integrations facilitate a holistic approach to security, encompassing both prevention and proactive detection.
Resources for AppSec Risk Management
Resources dedicated to Application Security (AppSec) risk management are invaluable for organizations aiming to fortify their networks against threats. These resources, including guidelines, best practices, and tools for detecting vulnerabilities, play a critical role in developing a robust security framework. They enable businesses to address the evolving landscape of cyber threats with confidence.
FAQs on Network Penetration Testing
Network penetration testing is a crucial practice for identifying and addressing security vulnerabilities within network and systems. It involves a comprehensive testing process that simulates real-world attacks on target systems to uncover weaknesses.
Why is Pen Testing Critical?
Penetration testing, or pen testing, is critical because it helps organizations identify and fix security issues before attackers can exploit them. This proactive approach is essential for protecting sensitive data, ensuring business continuity, and maintaining customer trust. Through pen testing, companies can better understand their security posture and make informed decisions to strengthen their defenses.
The Difference Between Pen Testing and Vulnerability Scanning
While both penetration testing and vulnerability scanning are essential for network security, there are key differences. Penetration testing involves a deliberate and in-depth exploration intended to exploit vulnerabilities and assess the actual risk to the system. In contrast, vulnerability scanning is an automated process that identifies potential vulnerabilities. Penetration testing offers a more nuanced understanding of security flaws, incorporating both external and internal perspectives, including external network penetration testing and internal penetration testing.
How Often Should Pen Tests Be Conducted?
The frequency of penetration testing depends on various factors, including the organization's size, complexity of the network, and sensitivity of the data handled. Generally, it's recommended to conduct pen tests annually or whenever significant changes are made to the network infrastructure. This ensures that new vulnerabilities are promptly identified and addressed, keeping the network secure.
Choosing the Right Pen Testing Service
Selecting the right penetration testing service is vital for achieving meaningful security outcomes. Organizations should look for providers with a proven track record, comprehensive testing methodologies, and the ability to offer actionable insights. It's also important to choose a service that aligns with the organization's specific needs, whether focusing on external network penetration testing, internal penetration testing, or both.
Navigating Challenges and Best Practices
Network penetration testing is fraught with challenges that require a fine balance between technical know-how and ethical practice. Best practices in this field not only demand a deep understanding of the latest vulnerabilities and threats but also necessitate a commitment to continuous learning and adaptation. As the digital landscape evolves, so too must the strategies and methodologies of penetration testers to ensure they provide the most comprehensive and effective security assessments possible.
Ethical Considerations and Legal Implications
When conducting testing activities, it's crucial to navigate the thin line between ethical hacking and potential legal breaches. Testers must have explicit permission from the organization owning the network before commencing any tests. This not only prevents legal repercussions but also ensures that all testing activities are conducted with integrity and respect for privacy and data protection laws. Ethical considerations form the backbone of trustworthy penetration testing, safeguarding both the tester and the client from unintended consequences.
Balancing Automated and Manual Testing Methods
In the realm of network penetration testing, striking the right balance between automated tools and manual testing methods is key to identifying potential weaknesses effectively. Automated tools can scan vast networks quickly, flagging issues for further investigation. However, they may not catch every nuance of a complex security system. Manual testing, on the other hand, allows for a more detailed and nuanced understanding of a network's vulnerabilities, though it requires significant time and expertise. The best approach combines both, leveraging the speed of automation with the depth of manual analysis.
Ensuring Comprehensive Coverage and Depth of Testing
Achieving comprehensive coverage and depth in testing is crucial for a thorough security assessment. This involves not only a wide-ranging examination across the network to identify vulnerabilities but also a deep dive into how these vulnerabilities could be exploited. It’s about understanding not just the breadth of potential security gaps but also the depth of the risk they pose. This level of thoroughness ensures that even the most hidden vulnerabilities are uncovered and addressed.
Continuous Improvement in Pen Testing Methodologies
The landscape of cybersecurity is ever-changing, and so the methodologies used in penetration testing must evolve accordingly. Continuous improvement is essential, with testers updating their strategies to incorporate the latest findings from vulnerability scans and adapting to new types of cyber threats. This iterative process not only enhances the effectiveness of penetration tests but also ensures that defenses are always a step ahead of potential attackers.
Future Trends in Network Penetration Testing
As digital threats become more sophisticated, the field of network penetration testing is rapidly evolving. Future trends point towards an increased reliance on artificial intelligence and machine learning to automate and refine testing processes. Additionally, the integration of new technologies promises to enhance the capabilities of testers, allowing for more dynamic and effective security assessments. Staying ahead of these trends is crucial for organizations looking to protect their networks from the ever-growing threat landscape.
The Evolution of Cyber Threats and Pen Testing Techniques
The cyber threat landscape is in a constant state of flux, with attackers continuously developing new methods to exploit network vulnerabilities. In response, penetration testing techniques are also evolving, employing more sophisticated tools and approaches to identify and mitigate these threats effectively. This ongoing arms race between attackers and defenders highlights the importance of adaptive, innovative testing strategies to safeguard digital assets.
The Role of AI and Machine Learning in Pen Testing
Artificial intelligence and machine learning are playing an increasingly pivotal role in network penetration testing. These technologies offer the potential to automate complex tasks, allowing for more efficient identification of vulnerabilities and prediction of potential attack vectors. By harnessing the power of AI and machine learning, testers can analyze vast amounts of data more accurately and swiftly, leading to more effective and timely security measures.
Enhancing Pen Testing with Emerging Technologies
The integration of emerging technologies into network penetration testing is set to revolutionize the field. From blockchain to quantum computing, these new tools offer unique advantages in enhancing security assessments. They provide innovative ways to test network defenses, ensuring that organizations can stay one step ahead of cybercriminals. The future of penetration testing lies in the ability to adapt and incorporate these cutting-edge technologies, offering unprecedented levels of network security.
The Critical Role of Network Penetration Testing in Today’s Digital World
In the digital age, where cyber threats evolve with alarming speed, network penetration testing emerges as a cornerstone of a robust cybersecurity strategy. By simulating real-world attacks, ethical hackers utilize a comprehensive array of tools and techniques, including port scanning and testing for vulnerabilities like buffer overflow, to uncover network vulnerabilities. This proactive approach enables security teams to identify and remediate security vulnerabilities before malicious actors can exploit them, safeguarding sensitive data against both external threats and internal threats. Moreover, penetration testing goes beyond mere risk assessments; it provides actionable insights into enhancing security measures, refining security policies, and fortifying application security across various platforms, including mobile applications. As businesses continue to navigate the complex cyber landscape, the role of penetration testing in maintaining a resilient defense against both known and emerging threats cannot be overstated. It embodies a critical layer of defense, ensuring that security checks, risk management, and mitigation strategies are always aligned with the organization’s evolving security needs.
Our Network Penetration information is here.

